By: Marcus Alexander
By: Marcus Alexander
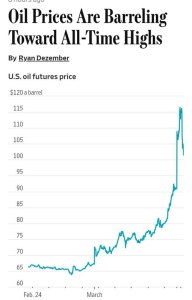
In a potential seismic shift in Middle Eastern geopolitics, major Gulf economies are reportedly considering withdrawing from contracts with the United States and reviewing future investment commitments to alleviate economic strain from the ongoing war with Iran.
The claims, which originated in a post on X by user Sulaiman Ahmed, suggest that Saudi Arabia, the United Arab Emirates, Kuwait, and Qatar are discussing measures to reduce their financial exposure to the U.S. economy. According to the post, which cites an anonymous official, the move is a direct response to “the economic strain imposed upon them by the Iran war.
These assertions are supported by a report published by Reuters on March 5, 2026, citing the Financial Times. The report confirms that Gulf states are indeed considering invoking force majeure clauses in current contracts and reviewing investment pledges made to the United States.
The decision appears to stem from a combination of reduced revenues and increased spending. The anonymous official cited in the original post noted that these countries face budget strains due to “reduced income from energy… the slowdown in output or the inability to ship,” as well as hits to the tourism and aviation sectors and a spike in defense spending.
This context is validated by broader economic analysis. JPMorgan recently trimmed its 2026 non-oil growth outlook for Gulf Cooperation Council (GCC) economies, pointing to rising regional risks following the latest escalation between the U.S., Israel, and Iran.
Strategists noted that economic life slowed sharply in major hubs like Dubai, Abu Dhabi, and Doha, raising near-term downside risks for services and broader non-oil activity.
Similarly, Fitch Ratings warned that while Gulf sovereigns can weather a short conflict, prolonged fighting or damage to energy infrastructure could threaten credit ratings. The agency noted that the Strait of Hormuz is effectively closed due to security threats, impacting energy exports.
Force Majeure and the Legal Context
The mention of “force majeure” is significant. A force majeure clause is a contractual provision that allows parties to be released from their obligations when extraordinary events beyond their control occur.
According to legal analysis from Aqran Vijandran Advocates & Solicitors, recent developments in the Middle East have placed force majeure at the centre of commercial contracts again, much like during the COVID-19 pandemic. Companies like QatarEnergy and Aluminium Bahrain have reportedly already invoked force majeure in response to the conflict.
Impact on US Relations and Global Investments
The financial stakes are immense. The original post correctly notes that these nations manage some of the world’s largest sovereign wealth funds and, following President Donald Trump’s visit to the region last year, pledged hundreds of billions of dollars in U.S. investments. A review of these commitments would likely catch the attention of the White House.
An adviser to a Gulf government, cited in the original text, confirmed that the prospect of such a review has already raised concerns in Washington. The Carnegie Endowment for International Peace observed that the Gulf states are confronting the limits of their ability to spend their way to influence at the White House, noting that President Trump appears unwilling to reshape his war-forward outlook despite Gulf opposition.
The potential redirection of Gulf capital extends beyond the United States. According to Semafor, the Middle East crisis risks upending burgeoning Gulf-Africa ties. Gulf nations have invested over $100 billion in Africa across energy, ports, and tech sectors, serving as a counterweight to Western and Chinese influence. However, sovereign wealth funds that have been pouring money into African projects may now redirect their attention and capital toward immediate domestic priorities and defense.
While the initial X post by Sulaiman Ahmed brought attention to the matter, the narrative is now backed by reports from major financial news outlets. Gulf states find themselves in an increasingly untenable position, caught between Iran’s retaliatory strikes and their security alliance with the U.S.
As budget strains mount and civilian infrastructure comes under fire, the wealthy Gulf monarchies appear to be considering economic self-preservation measures that could fundamentally alter their relationship with the United States and the global economy